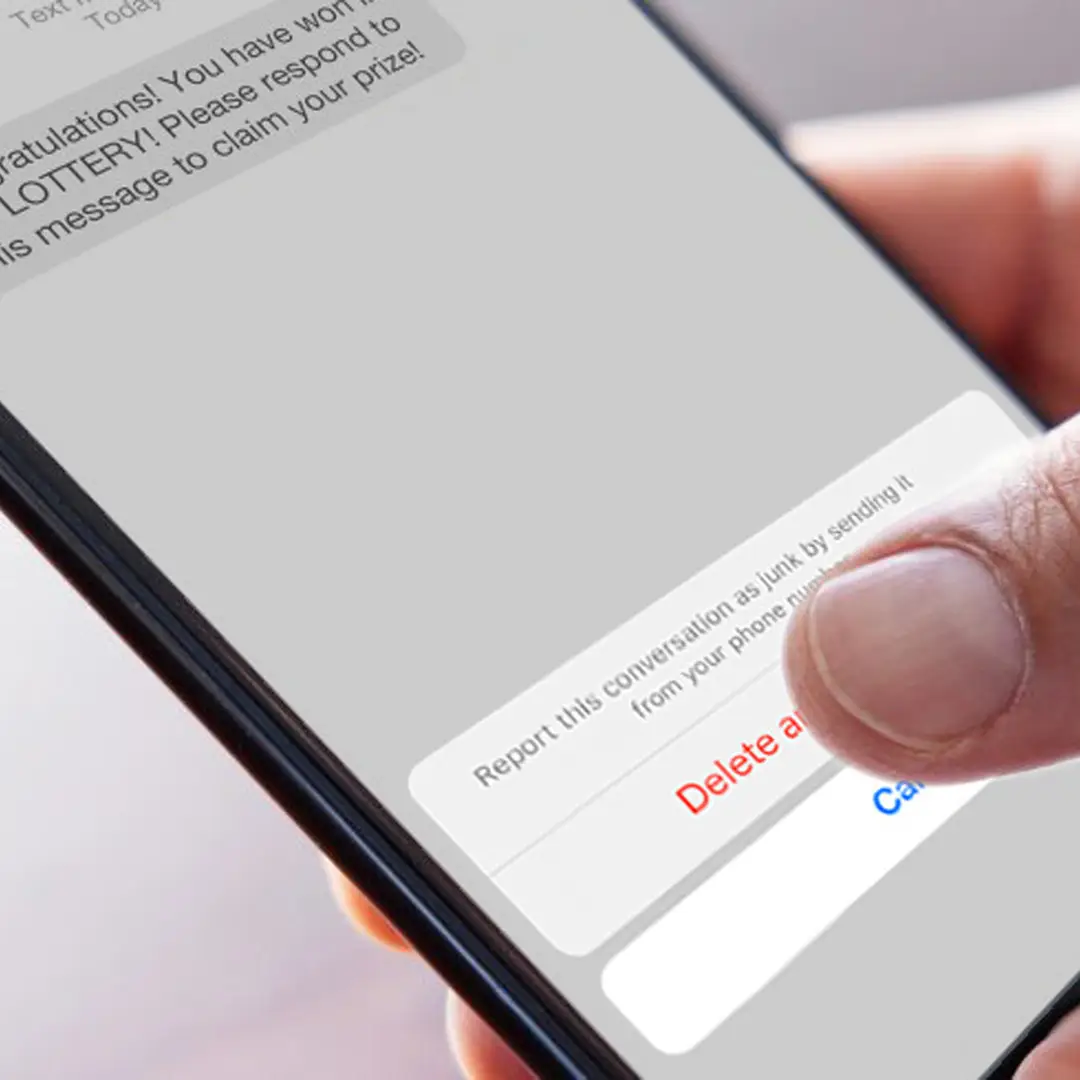
The ongoing battle against cybercrime intensifies as scammers exploit new technologies, and the latest tool to raise alarm bells is Xeon Sender. This cloud-based platform is being increasingly used to orchestrate extensive SMS phishing and spam campaigns, taking advantage of otherwise legitimate services.
According to a SentinelOne researcher, “Attackers can use Xeon to send messages through various SaaS providers using valid credentials”. This means that rather than hacking into these systems, scammers are manipulating them by exploiting valid credentials and the services’ functionalities.
Services being misused for these bulk SMS operations include well-known platforms such as Amazon SNS, Nexmo, Plivo, Proovl, Send99, Telesign, Telnyx, TextBelt, and Twilio. What is particularly concerning is that Xeon Sender does not exploit vulnerabilities within these services. Instead, it abuses their legitimate APIs to facilitate mass SMS spam campaigns. This method not only bypasses traditional security mechanisms but also leverages the trusted reputation of these services to evade detection.
Xeon Sender is a troubling trend in cybersecurity, where tools like SNS Sender are being specifically designed for large-scale smishing operations. These operations aim to deceive individuals into divulging sensitive personal information, such as passwords or financial details. Xeon Sender is distributed through Telegram and hacking forums, with its latest version connected to a Telegram channel known as Orion Toolxhub. This channel not only distributes Xeon Sender but also offers other malicious tools, including brute-force attackers and Bitcoin clippers.
Known alternatively as XeonV5 or SVG Sender, Xeon Sender was first identified in early 2022. Since its inception, it has undergone various adaptations by different threat actors. Some versions of the tool are hosted on web servers with a “easy-to-use” GUI (graphical user interface), making them more user-friendly, especially for those who might not be proficient with Python-based tools.
The tool features a command-line interface that interacts with backend APIs to facilitate bulk SMS attacks. It incorporates functionalities for validating account credentials, generating phone numbers, and verifying their validity. Despite its seemingly straightforward nature, the tool’s source code is designed with ambiguous variables, making debugging and detection particularly challenging. The use of provider-specific Python libraries adds another layer of complexity, as these libraries vary across different services and contribute to unique detection challenges due to differing logs and library structures.
To mitigate the risks presented by phishing tools like Xeon Sender, organizations should implement robust monitoring strategies for SMS sending permissions. It is crucial to be vigilant for any unusual activities, such as unexpected large uploads of new recipient phone numbers or significant spikes in message volumes. By maintaining a proactive stance and closely monitoring for anomalies, organizations can better defend against these sophisticated spam and phishing campaigns.